Cloud Security & Compliance | Shielded by Design

Cloud-Native. Risk-Ready. Compliance-Driven.
We help organizations deploy secure cloud environments with compliance-ready architecture (SOC2, HIPAA, GDPR). Our approach blends DevSecOps, zero trust, and continuous audit readiness.
Key Features:
- 👤 Cloud Identity & Role Management
- 🚫 Zero Trust Network Access (ZTNA)
- 🧾 Audit Logs & SIEM Integration
- 🔐 Data Encryption – At Rest & In Transit
- 🛡️ Penetration Testing & Vulnerability Scanning
- 📄 Compliance Frameworks – SOC 2, ISO 27001, HIPAA
- 🧱 Policy-as-Code & Guardrails
As IBM’s Cost of a Data Breach Report shows, cloud misconfigurations are the top attack vector in breaches. We close those gaps with proactive security architecture.
Security is Not a Feature — It’s a Framework
From IAM to audit logs and network segmentation, our solutions are built for compliance and long-term resilience.
Benefits
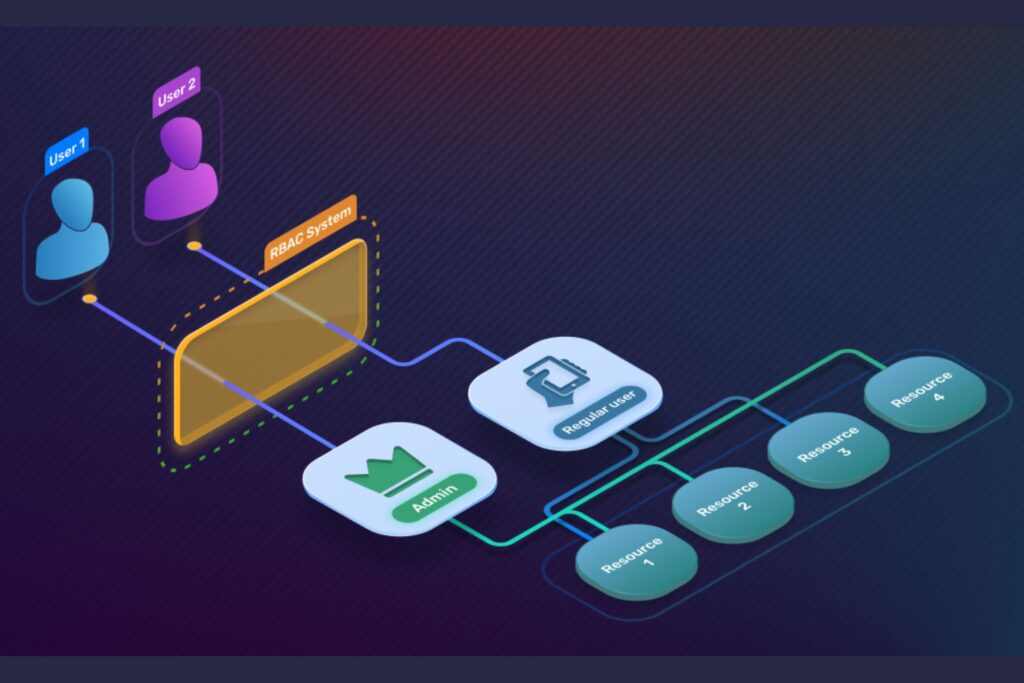
Role-Based Access Control

Automated Security Scans
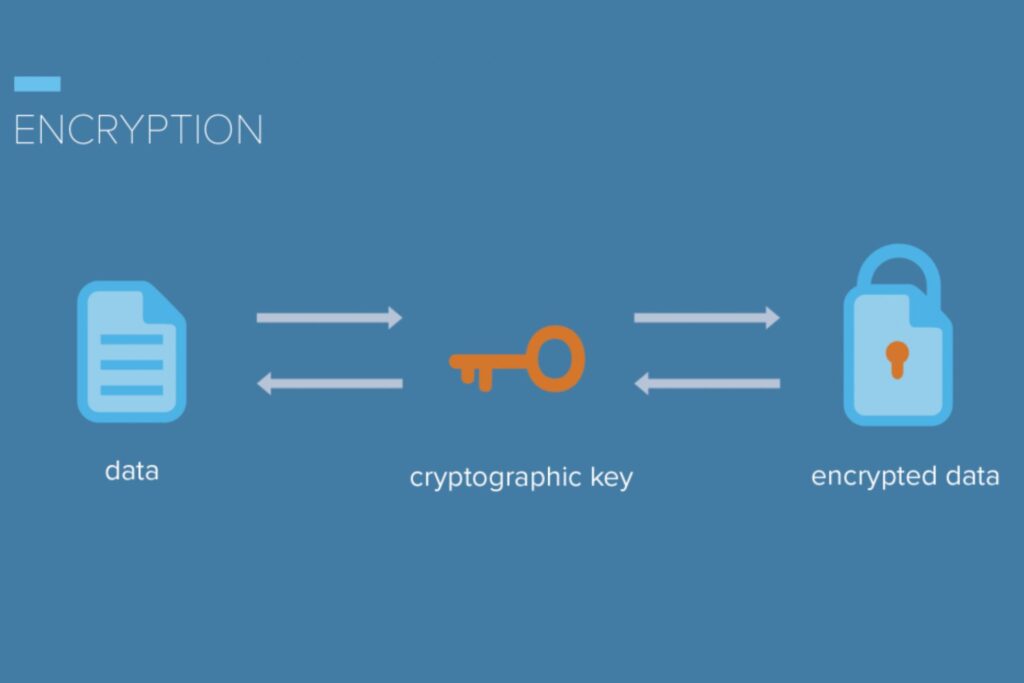
Encryption with Key Rotation

Compliance-Ready Audit Trails
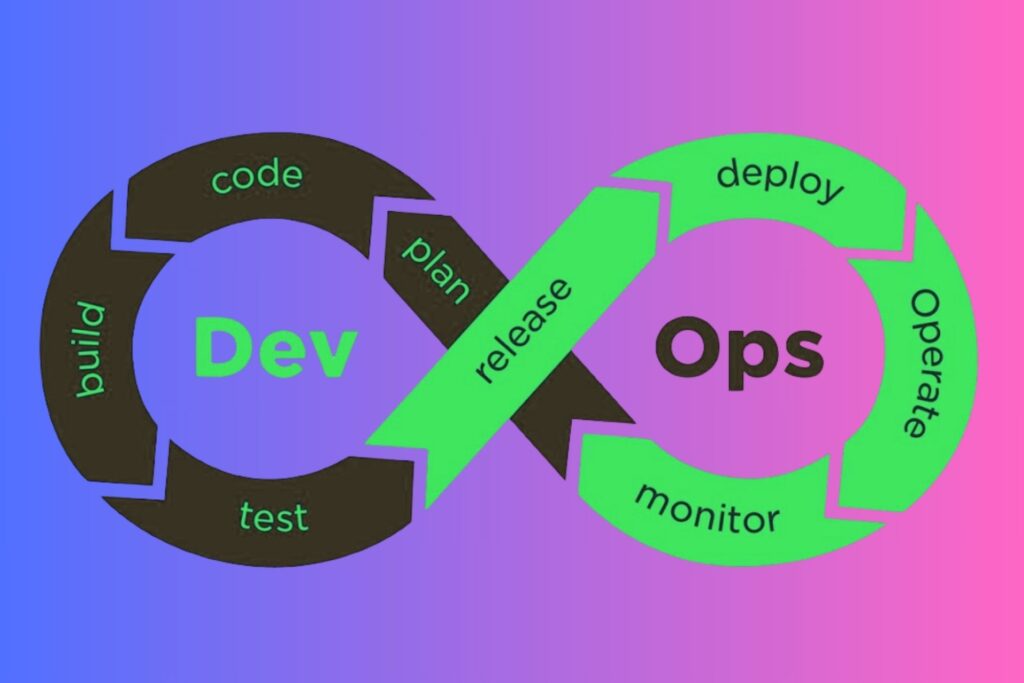
DevSecOps Workflow Integration

SSO, MFA & Identity Federation
Have Questions? We’ve Answers
Answer to your Queries
Can you help us achieve SOC2 or HIPAA compliance?
Yes. We offer infrastructure hardening, logging, and documentation required for both audits.
Do you implement Zero Trust architecture?
Yes. We use ZTNA with policy enforcement, network microsegmentation, and least-privilege access.
What tools do you use for monitoring and alerts?
We set up CloudTrail, Datadog, GuardDuty, and SentinelOne based on your needs.
How often should we audit cloud security?
We recommend quarterly audits with daily alerting and monthly vulnerability scans.
Is multi-factor authentication included?
Yes. We enforce MFA across all user access layers and integrate with Okta or Auth0.
More Services
Boost your online presence with SEO, SEM, and performance marketing strategies.
Guide your digital transformation with expert strategies to stay ahead in a competitive world.
Leverage data and AI for actionable insights that drive smarter business decisions.
